Enforce policies and apply secure password usage
Make sure that secure password behavior is the default
Prevent unsafe behavior — right when it's necessary


Make safe behavior the only option

Demonstrate control over compliance


From password policy on paper to action in practice
Password Manager 2.0
With our three-step approach — Identify, Improve, Insist — you tackle the problem at the core. Structural and effective.
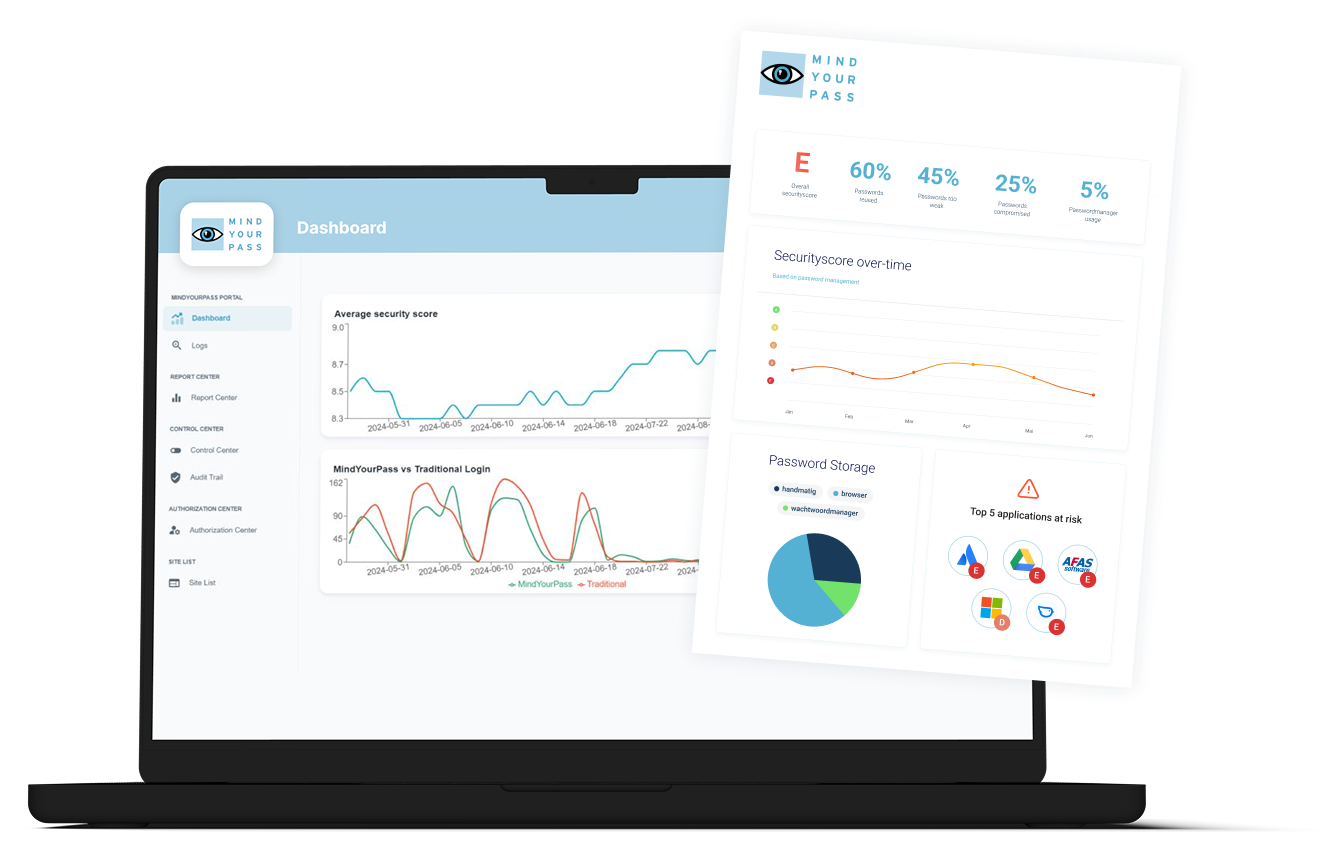
See how secure your logins really are
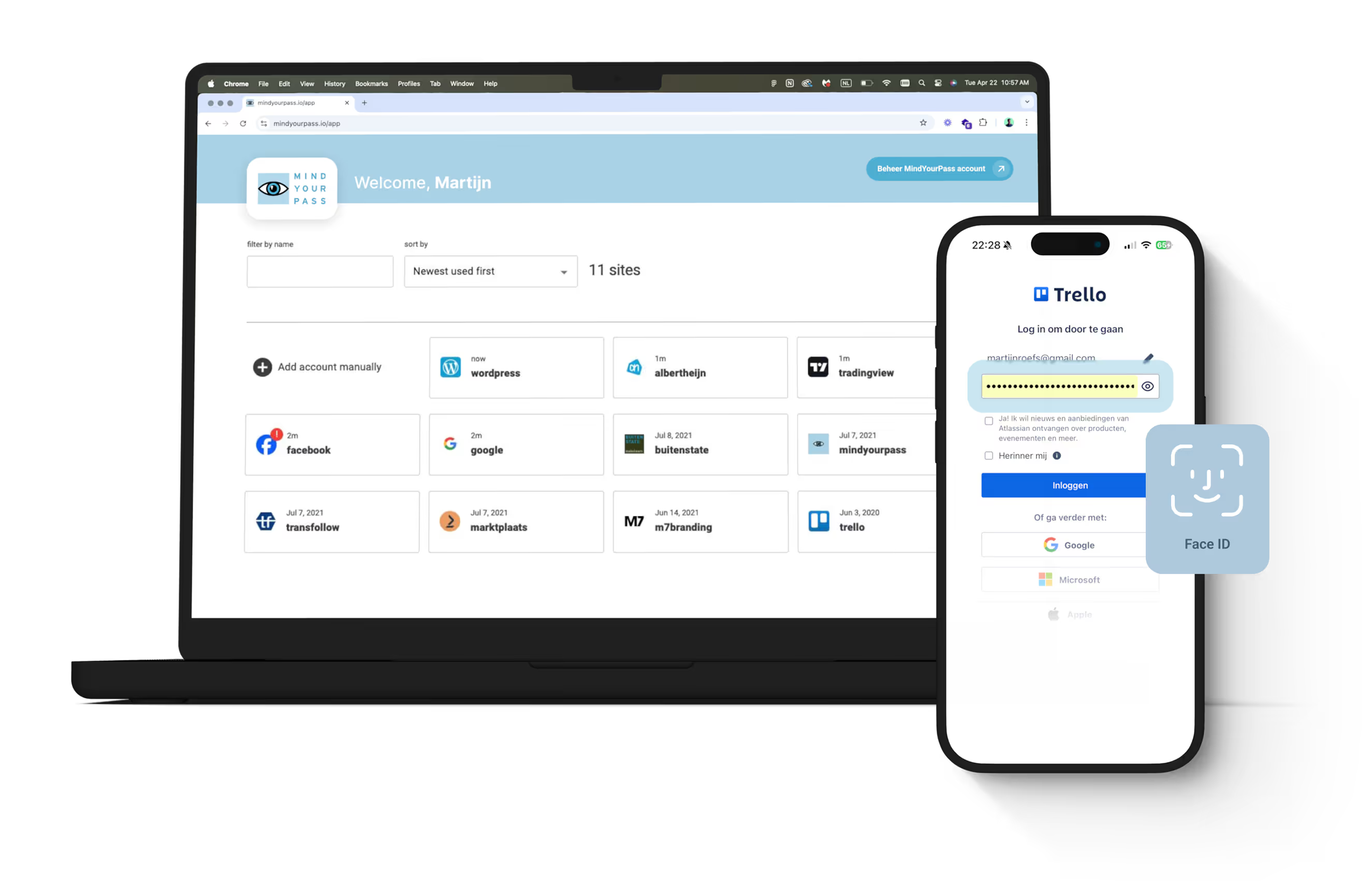
A password manager people really use
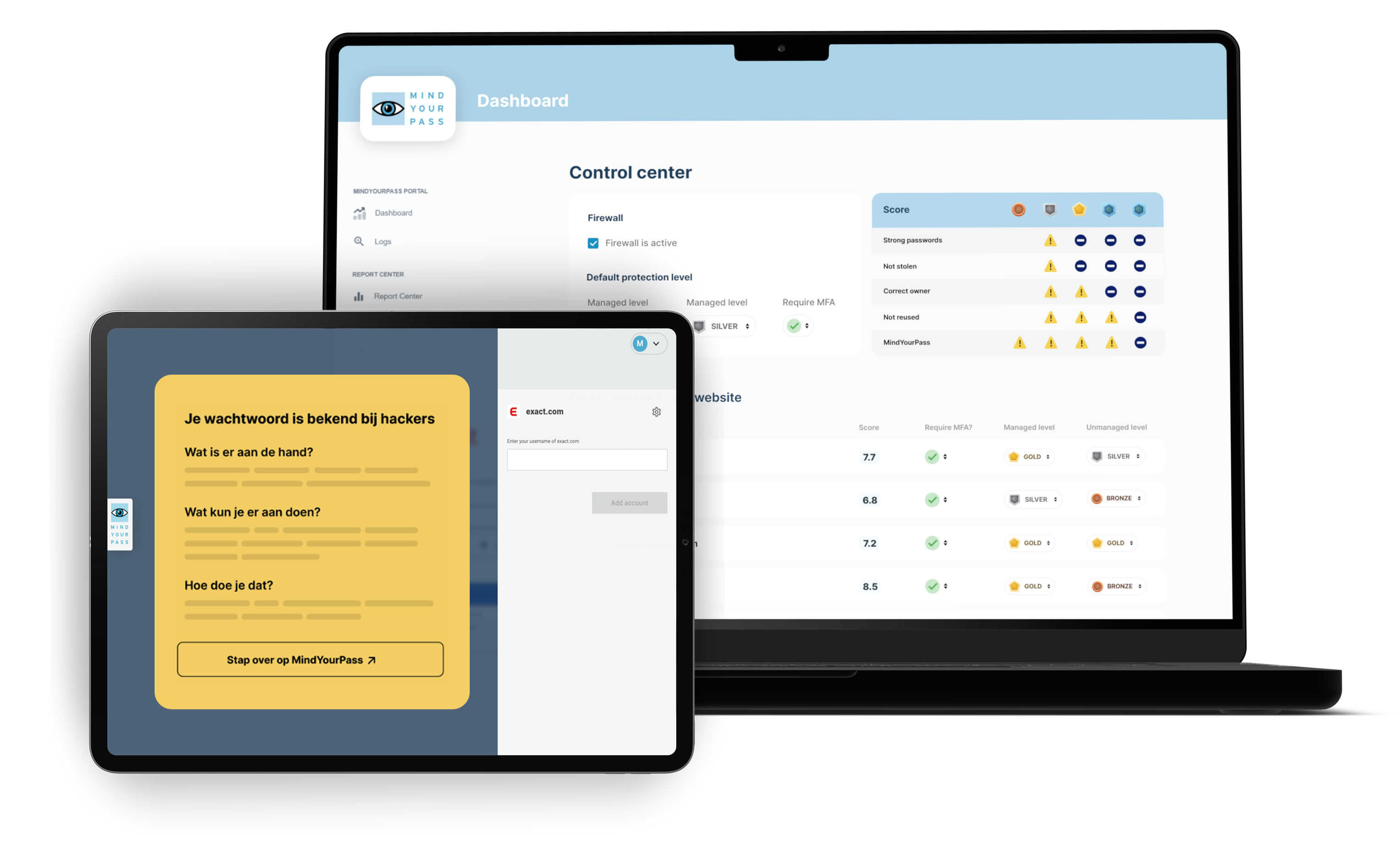
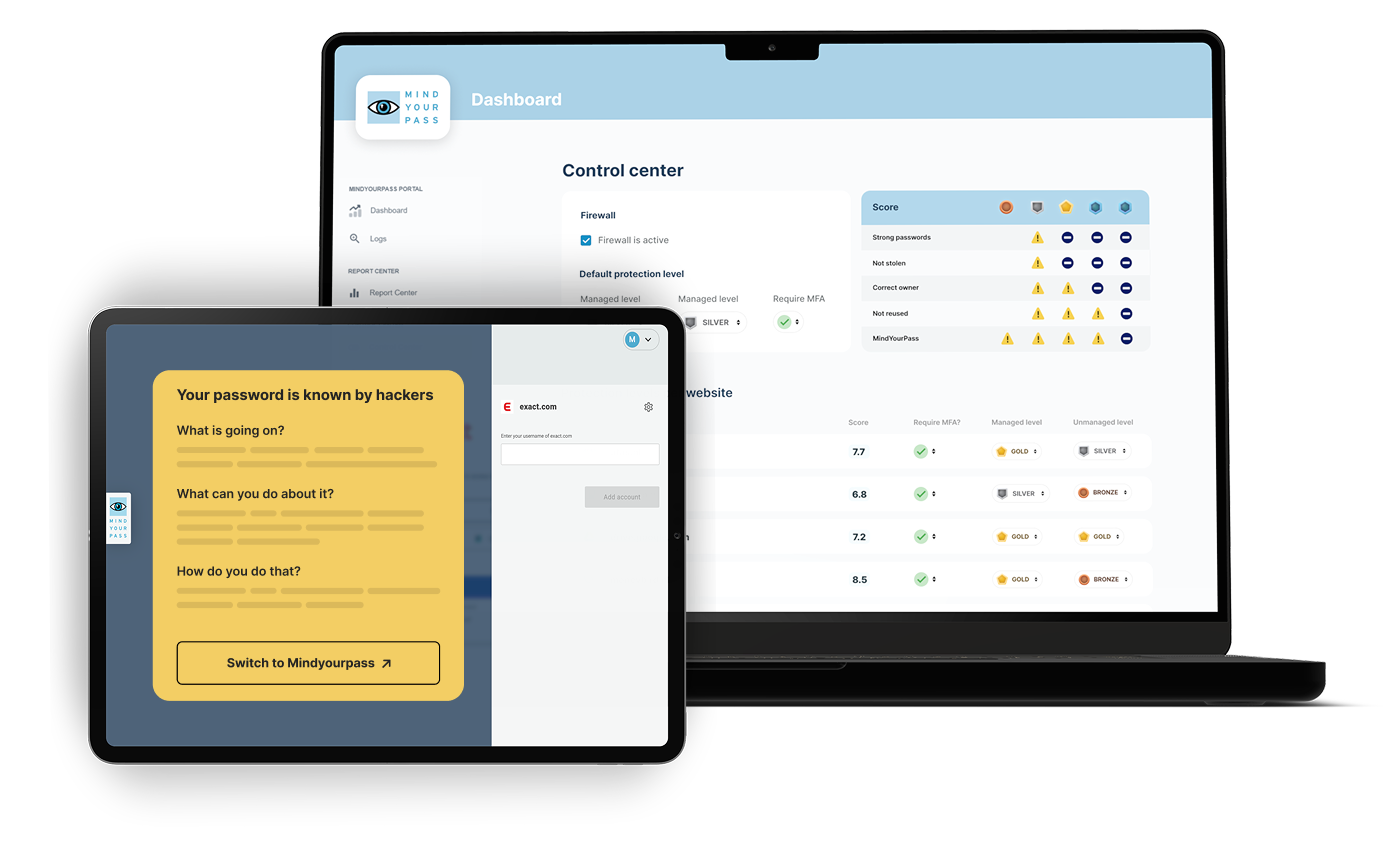
From policies on paper to practice
Logging in securely requires more than just a tool

With the browser-based baseline measurement, you get insight into the actual password behavior within your organization.
Centrally manage access to business passwords when onboarding and offboarding users
Restrict access to applications anytime or when passwords don't comply with policies
Only allow the use of the organization's password manager. Also works with 3rd party password managers.
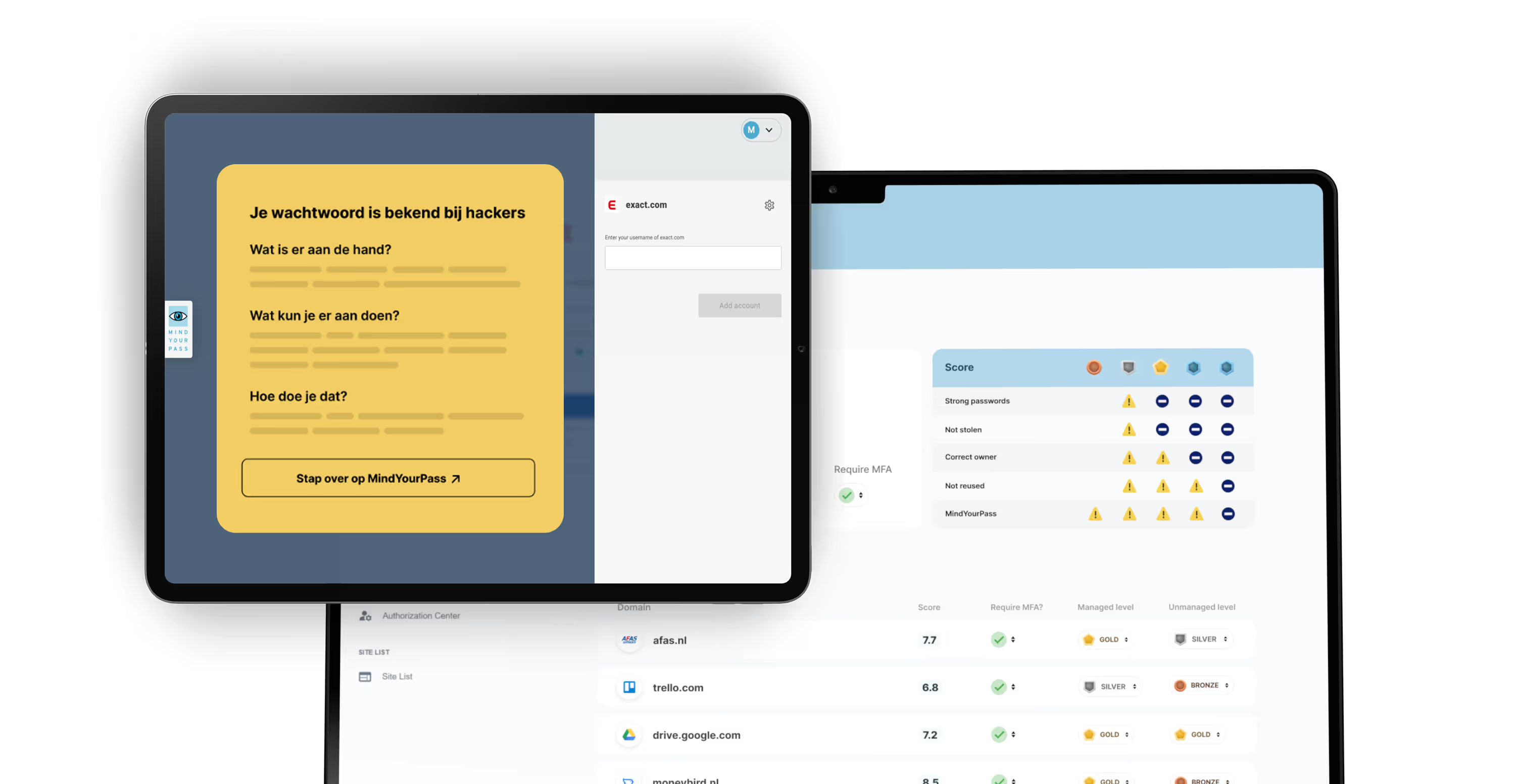
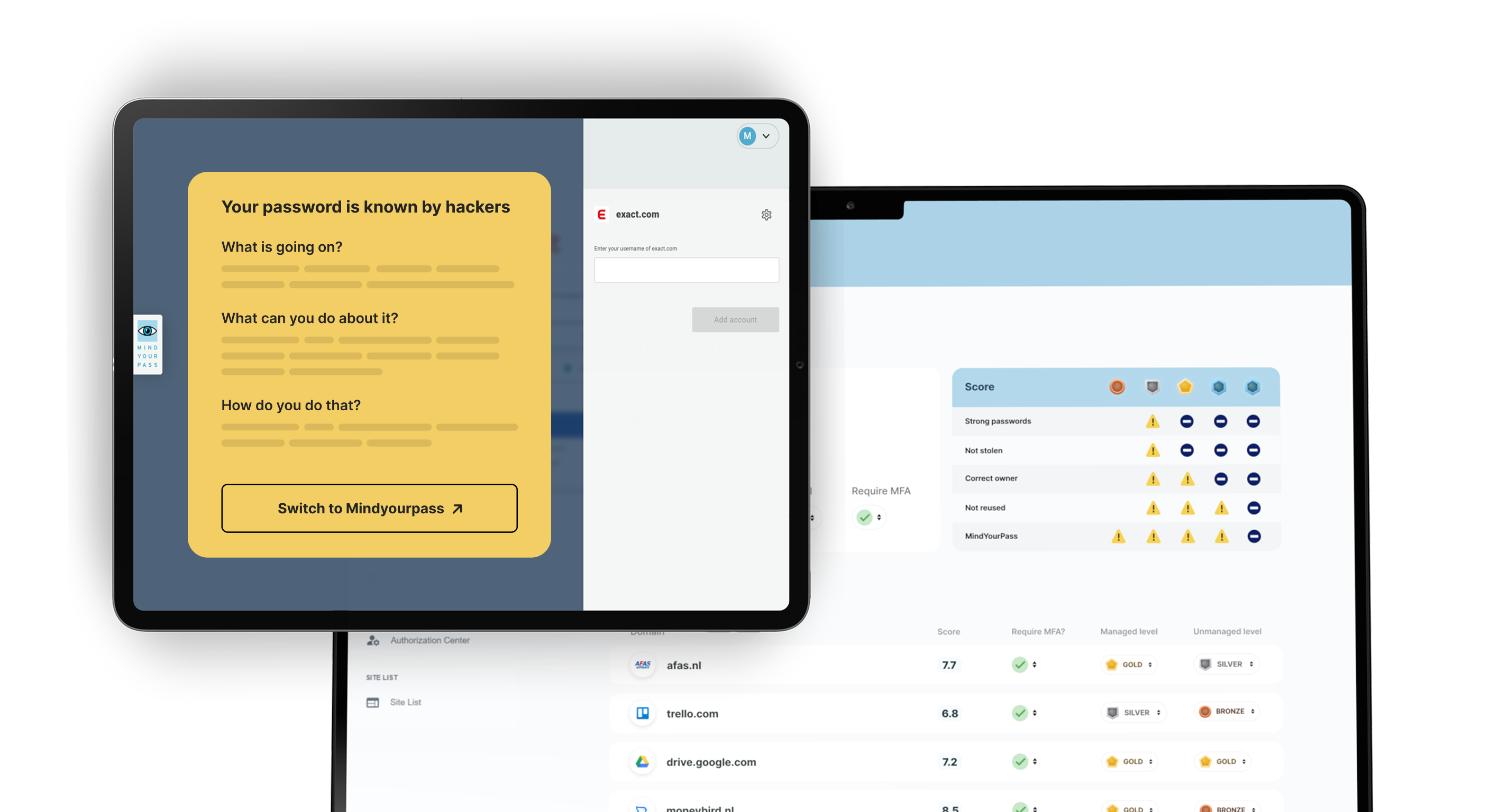
Always ensure that employees comply with the password policy by enforcing the use of secure passwords for each application.
Privacy guaranteed — always
The baseline measurement takes 4 weeks. After this period, we have sufficient measurement results to prepare the report.
By insisting, password policies no longer become a set of paper rules of conduct, but a daily practice. Everyone works with the same secure password manager and always according to the password policy, so safe behavior remains the norm. This way, as an organization, you can maintain control over password use and you can easily demonstrate that you meet all compliance requirements. In short, 100% adoption and 100% secure passwords.
Policies are easily adjustable per site or application, or at one of the standard levels: business applications and non-business (private) applications. The policies are automatically active for the sites and applications concerned and the users.
No. As an organization, you decide whether and where to enforce MindYourPass, and what password requirements you use. Prefer not to enforce? Then you can also set alerts only.
In the MindYourPass Portal, as an administrator, you set policies for:
- Mandatory use of MindYourPass for password management and login
- Mandatory password management under the correct identity (separating business and private)
- Mandatory password policy compliance (length/complexity, unique, uncompromised)